Note: For the BlueApp to send response actions, you must have a Cisco Umbrella package that supports the Enforcement API. See the vendor website for more information about the Cisco Umbrella product packages.
| Action | Description |
|---|---|
| Report names found on an alarm | Run this action to send the alarm information to your Cisco Umbrella environment. This action is available only when you launch an app action directly from an alarm. |
| Report by a HTTP hostname found on an event | Run this action to send the HTTP hostname associated with an event to your Cisco Umbrella environment. This action is available when you launch an app action in an orchestration rule. |
| Report by an URL found on an event | Run this action to send the URL associated with an event to your Cisco Umbrella environment. This action is available when you launch an app action in an orchestration rule. |
| Report by a DNS record found on an event | Run this action to send the DNS associated with an event to your Cisco Umbrella environment. This action is available when you launch an app action in an orchestration rule. |
- In USM Anywhere, go to Data Sources > BlueApps.
- Click the Available Apps tab.
- Search for the BlueApp, and then click the tile.
- Click the Actions tab to display information for the supported actions.
- Click the History tab to display information about the executed orchestration actions.
Launch Actions from USM Anywhere
If you want to apply an to similar events that occur in the future, you can also create orchestration rules directly from an action applied to an alarm, event, or vulnerability. To launch a Cisco Umbrella orchestration action for an alarm or event- Go to Activity > Alarms or Activity > Events.
- Click the alarm or event to open the details.
-
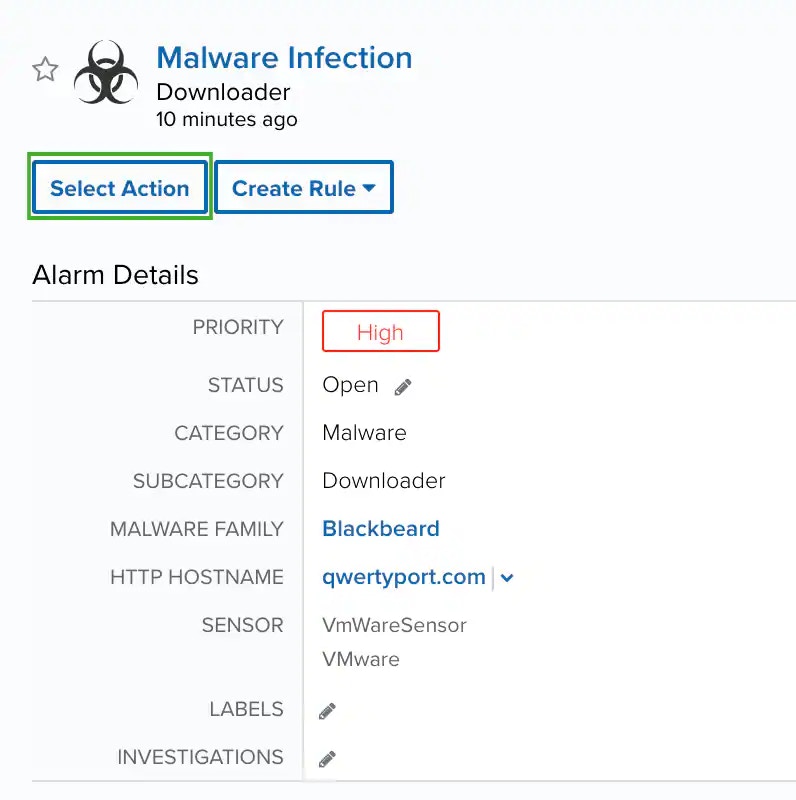
Click Select Action.
-
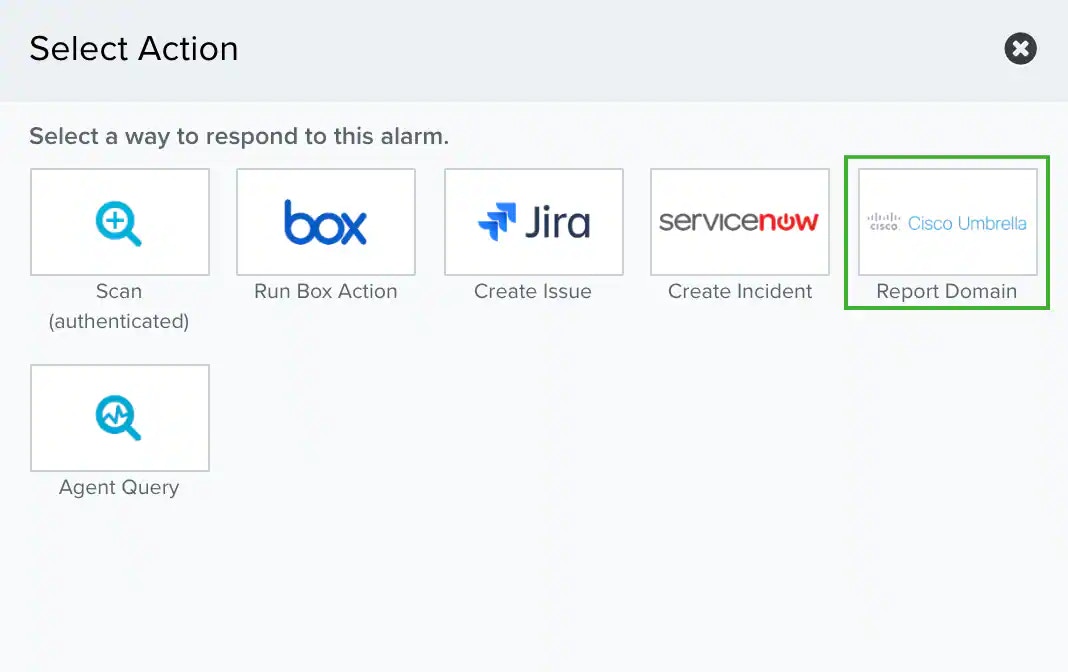
In the Select Action dialog box, select the Cisco Umbrella tile.
-
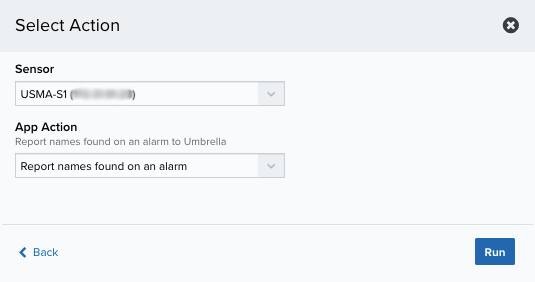
If you have more than one sensor installed, select the sensor where the BlueApp for Cisco Umbrella is enabled.
-
Click Run.
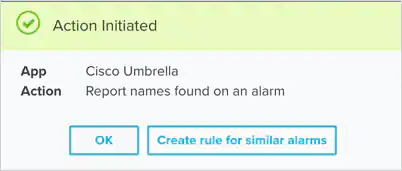
After USM Anywhere initiates the action, it displays a confirmation dialog box.
If you want to create a rule to apply the action to similar items that occur in the future, click Create rule for similar alarms or Create rule for similar events and define the new rule. If not, click OK.