| Role Availability | Read-Only | Investigator | Analyst | Manager |
General Guideline
When creating an orchestration rule, you must specify an item you want to match and your matching criteria. Depending on the type of rule, the matching item can be , logs (), configuration issues, vulnerabilities, system events, or console user events. Your matching criteria is called rule conditions in USM Anywhere. Each rule condition contains three parts: a field, an operator, and a value.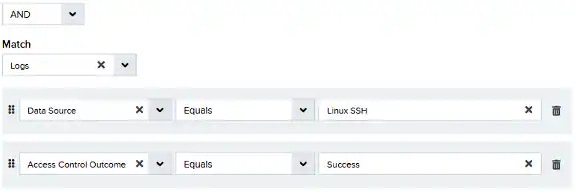
Best Practice on Rule Conditions
As you add different conditions to your rule, USM Anywhere converts them into query strings and displays them in the same order as added under Current Rule.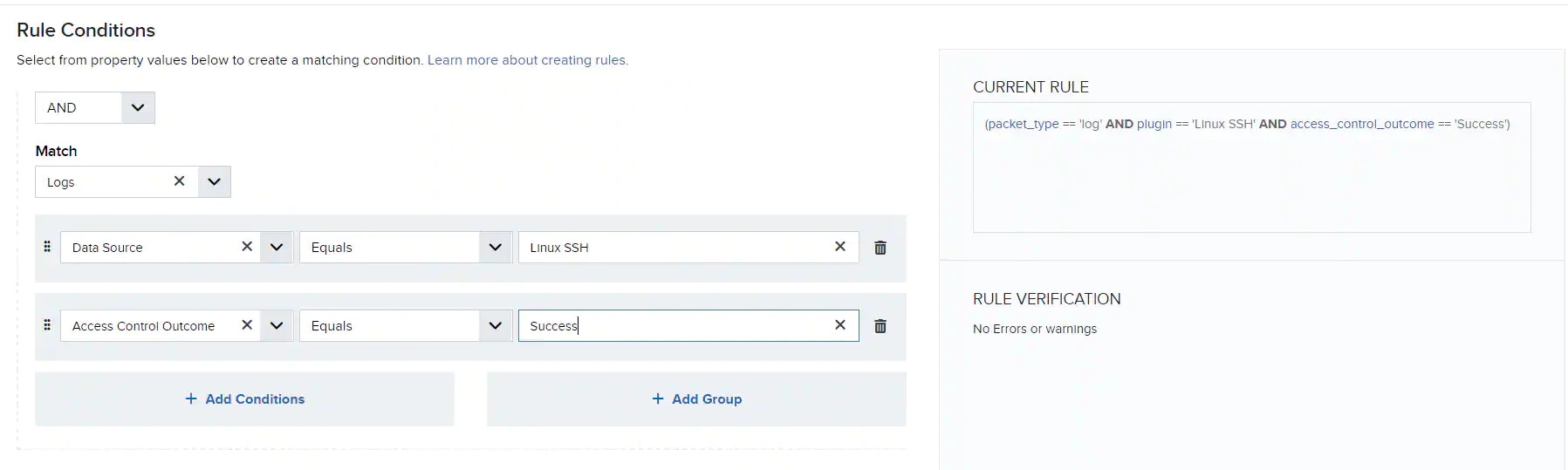
-
To ensure efficient processing, all rules should contain at least two conditions, one for
packet_typeand the other for plugin.packet_typeis the internal field name for the item you are matching against, while plugin is the internal field name for Data Source. - Place the most restrictive condition immediately after Data Source to save time processing the conditions.
-
Use
Equalsfor string comparison (case sensitive) as much as possible because it consumes the least resources. -
Evaluate your conditions carefully (from left to right) to make sure that it isn’t always true or always false.
For example, the following rule is always false:
On the other hand, a rule with the following conditions is always true:
-
Reduce the total number of rules. Avoid having multiple rules with the same conditions to reduce resource consumption.
For example, if there are the following two rules:
Rule 1:
Rule 2:It’s better to combine them into one rule:
-
Do not add extra fields or conditions in the rule that have no bearing on the result. For example:
The last condition is unnecessary because all SSH attempts use pluggable authentication modules (PAM) for authentication.
Best Practice on Rule Operators
USM Anywhere supports a wide range of operators when creating orchestration rules. Some operators require more resources to process than others; therefore, LevelBlue also provides some guidelines on choosing the best operators for your rules:- Always use case sensitive comparators where available. Equals, Not Equals, Contains, Assign or Equals, In, Match, In List, and Not In List offer both case-sensitive and case-insensitive comparisons.
-
If you want to match a specific string, use Equals instead of Contains.
Use:
Do not use:
-
Use IN instead of multiple Equals and OR combinations for the same field.
Use:
Do not use:
-
Use a Correlation List and the In List operator where possible. For example:
Note: You can’t use correlation lists in filtering rules.
-
If you want to match a field with no values, use the Is Empty operator.
This is how the LevelBlue Generic Data Source events are identified. Search for events where the Data Source field is empty. The AlienVault Generic Data Source is not a valid data source name. Use it as
plugin == “”for the Data Source Event field, which means that the data source is empty. See USM Anywhere Rules - Use of “AlienVault Generic Data Source” in Orchestration Rules for more information. - Use Contains instead of Match. The Match operator requires a valid regular expression (regex) as the value. Using a malformed regex to search a large raw log can cause performance degradation. If you have to use Match, form a simple regex and place this condition as the last one in your rule.
- Avoid using OR, OR NOT, and AND NOT operators unless absolutely necessary. It’s very easy to create always-true or always-false conditions when using these operators.
-
Do not use
packet_payloadevent detail for rule criteria because the rule will not validate as true. Use raw log event details if you need them, which consist of the packet syslog header followed by the packet payload data. The use of this event detail generates a warning message in the rules user interface (UI) views. Specifypacket type==logto have a valid rule. Alarm rules do not have access to this data field and will never validate as true.