| Role Availability | Read-Only | Investigator | Analyst | Manager |
- Go to Environment > Vulnerabilities.
- Search for the vulnerability for which you want to launch an authenticated scan.
- Click the vulnerability.
- The vulnerability details dialog box opens with the information about the specific vulnerability.
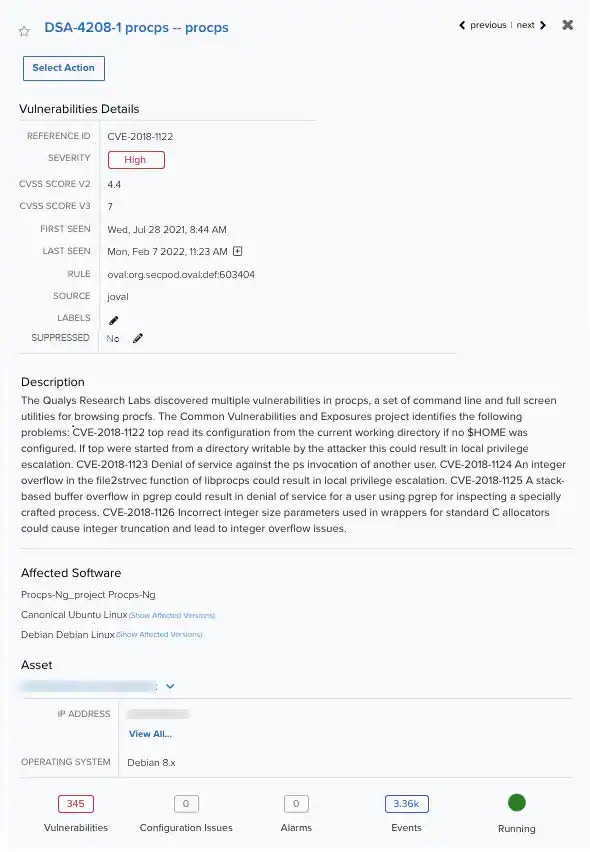
- Click Select Action.
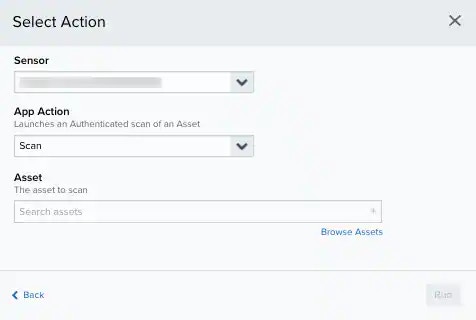

- Depending on the selected option, you should fill in different fields.
- Click Run.