| Role Availability | Read-Only | Investigator | Analyst | Manager |
- Go to Environment > Vulnerabilities.
-
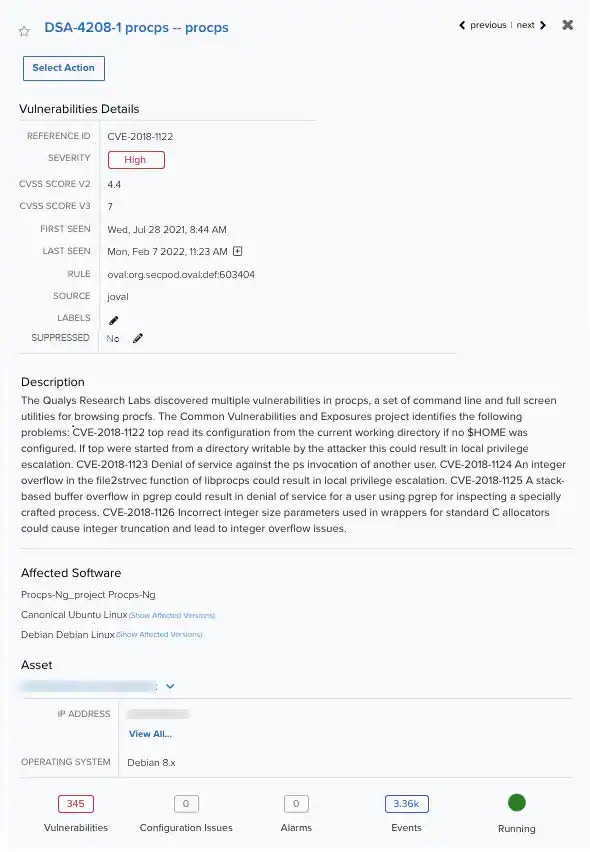
Click the to display a summary view, and then click the vulnerability name to open the full details of the vulnerability.
Click the
icon to bookmark an item for quick access.
The Vulnerabilities Details page includes the Select Action button that is supported for your assigned user . Use this button to launch an authenticated scan. See Applying Actions to Vulnerabilities for more information. You can see the vulnerabilities details, then a description, the affected software, and the associated asset. If you want more information, click theNote: You can view your bookmarked items by going to the secondary menu and clicking theicon. This will display all of your bookmarked items and provide direct links to each of them.
icon. See Viewing Assets Details for more information. The Labels field indicates if the vulnerability has been classified by using a label. You can click the
icon to manage the labels of the vulnerability. See Labeling the Vulnerabilities for more information. The Suppressed field enables you to indicate whether this vulnerability has been suppressed. You can click the
icon to select a suppression option (Yes or No). A vulnerability marked Yes will continue to be marked as suppressed on all future scans or until this field is updated.
- In the upper right corner, click Previous and Next to navigate between items.
-
Click the
icon to close the dialog box.
- Click the vulnerability title to expand its details.