- Go to Activity > Alarms.
-
Click the alarm to display a summary view, and then click the alarm name to open the full details of the alarm.
Click the
icon to bookmark an item for quick access.
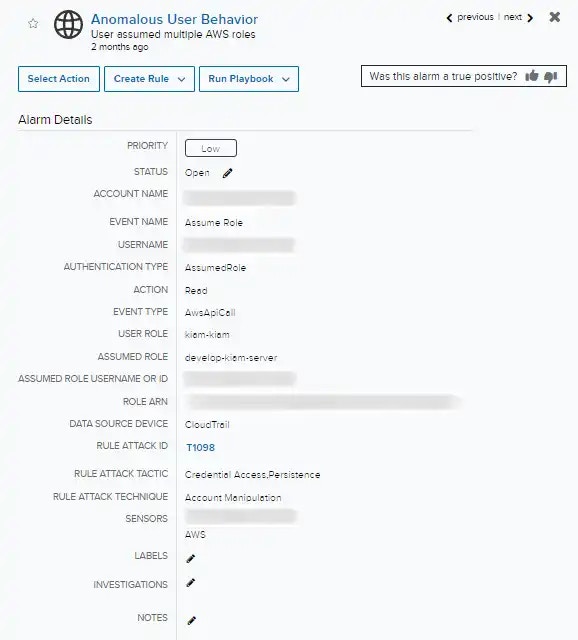
Not all alarms found during monitoring are necessary in managing your environment because they do not pose a security threat. It is common for low priority alarms to create noise, which can make it difficult to monitor alarms that require more attention. You can identify these alarms and suppress them by using a rule. The Alarms Details page includes alarm management functions that are supported for your assigned user role:Clicking theicon on the secondary menu shows the bookmarked items and provides links to them.
- Select Action: See Applying Actions to Alarms for more information.
- Create Rule: See Creating Rules from Alarms for more information.
- Generate Report: See Create an Alarms Report for more information.
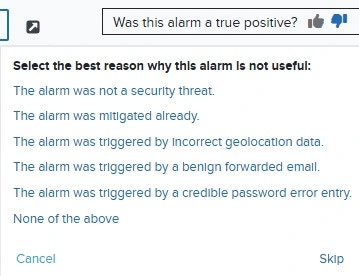
- Was this alarm a true positive?: Click the
 or
or  icon to apply an alarm outcome of True Positive or False Positive. If this alarm was a False Positive, select an optional reason from the drop-down list. Leave these icons unselected to retain a status of Undetermined.
icon to apply an alarm outcome of True Positive or False Positive. If this alarm was a False Positive, select an optional reason from the drop-down list. Leave these icons unselected to retain a status of Undetermined.
 The alarm details include the main fields that identify an alarm. You can edit or add values into these fields:Once specified, the reason an alarm was not useful cannot be viewed in the Alarm Details. It can only be checked through the Alarms Explorer page by adding the Alarm Outcome Reason filter, or by using the related Console User Events generated for that action.
The alarm details include the main fields that identify an alarm. You can edit or add values into these fields:Once specified, the reason an alarm was not useful cannot be viewed in the Alarm Details. It can only be checked through the Alarms Explorer page by adding the Alarm Outcome Reason filter, or by using the related Console User Events generated for that action.- Status: This field indicates the status for the alarm: Open, In Review, or Closed. You can click the
icon to edit the field and apply a status. See Alarm Status for more information.
- Labels: This field indicates if the alarm has been classified by using a label. You can click the
icon to manage the labels of the alarm. See Labeling the Alarms for more information.
- Investigations: This field indicates if the alarm has been associated to an investigation. You can click the
icon to edit the field and enter the title or the number that identifies each investigation. See Adding an Alarm to an Investigation for more information.
- Notes: This field allows you to enter notes regarding this alarm. You can click the
icon to enter text into this field.
- HTTP Hostname: If the alarm includes this field, you can search for events by using it. See Searching Events from the Details of an Alarm for more information.
- DNS RR Name: If the alarm includes this field, you can search for events by using it. See Searching Events from the Details of an Alarm for more information.
icon located next to the source and destination fields allows you to access these options:
- Search Pivot: Identify alarms triggered in the last hour, 24 hours, 7 days, 30 days, or 90 days. You can also configure your own period of time by clicking the Custom Range option. When you click the icon, a calendar opens. You can choose the first and last day to delimit your search by clicking the days on the calendar or entering the days directly. Then select the hours, minutes, and seconds by clicking the specific box. Finally, select AM or PM.
- Find Source or Destination in Events: Use this link to search events having the same source or destination as the alarm.
- Find Source & Destination in Events: Use this link to search events having the same source and destination as the alarm.
icon located next to the asset enables you to access the following options. Your access to these options may vary based on your user role. See Role-Based Access Control (RBAC) in USM Anywhere for more information:
- Add to Current Filter: Use this option to add the asset name as a search filter. See Searching Alarms for more information.
- Find in Events: Use this option to execute a search of the asset name in the Events page. See Events List View for more information.
- Look Up in OTX: This option searches the IP address of the source asset in the Open Threat Exchange page. See Using OTX in USM Anywhere for more information.
- Add Asset to System: Use this option to create the asset in the system. See Adding Assets for more information.
TheThe value in the FQDN field comes from the event itself (raw log). This field can have a real FQDN, an IP address, or be empty.icon located next to the asset enables you to access the following options. Your access to these options may vary based on your user role. See Role-Based Access Control (RBAC) in USM Anywhere for more information:
- Add to Current Filter: Use this option to add the asset name as a search filter. See Searching Events for more information.
- Find in Events: Use this option to execute a search of the asset name in the Events page. See Searching Events for more information.
- Look Up in OTX: This option searches the IP address of the asset in the OTX page. See Using OTX in USM Anywhere for more information.
- Full Details: See Viewing Assets Details for more information.
- Configure Asset: See Editing Assets for more information.
- Delete Asset: See Deleting the Assets for more information.
- Assign Credentials: See Managing Credentials in USM Anywhere for more information.
- Authenticated Scan: This option displays depending on the USM Anywhere Sensor associated with the asset. See Running Authenticated Asset Scans for more information.
- Scan with BlueApp: This option enables you to run an asset scan through an BlueApp. See Running Asset Scans Using a BlueApp for more information.
- Configuration Issues: This option opens the Assets Details page. The Configuration Issues tab is selected in the page. See Viewing Assets Details for more information.
- Vulnerabilities: This option opens the Assets Details page. The Vulnerabilities tab is selected in the page. See Viewing Assets Details for more information.
- Alarms: This option opens the Assets Details page. The Alarms tab is selected in the page. See Viewing Assets Details for more information.
- Events: This option opens the Assets Details page. The Events tab is selected in the page. See Viewing Assets Details for more information.
- Click the link of an associated event to open its details page. The Associated Events list displays all events associated with the alarm.
- In the upper right corner, click Previous and Next to navigate between items.
-
Click the
icon to close the dialog box.
See the Searching Events from the Details of an Alarm page for more information about the options in the HTTP Hostname, DNS RR Name, Source, and Destination fields.